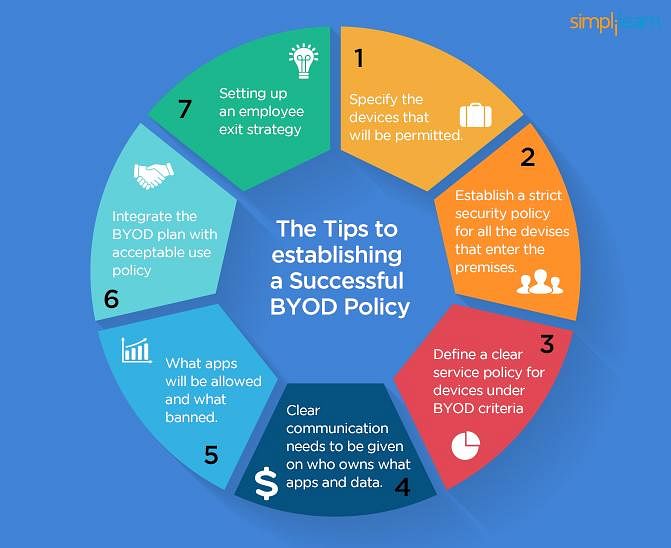
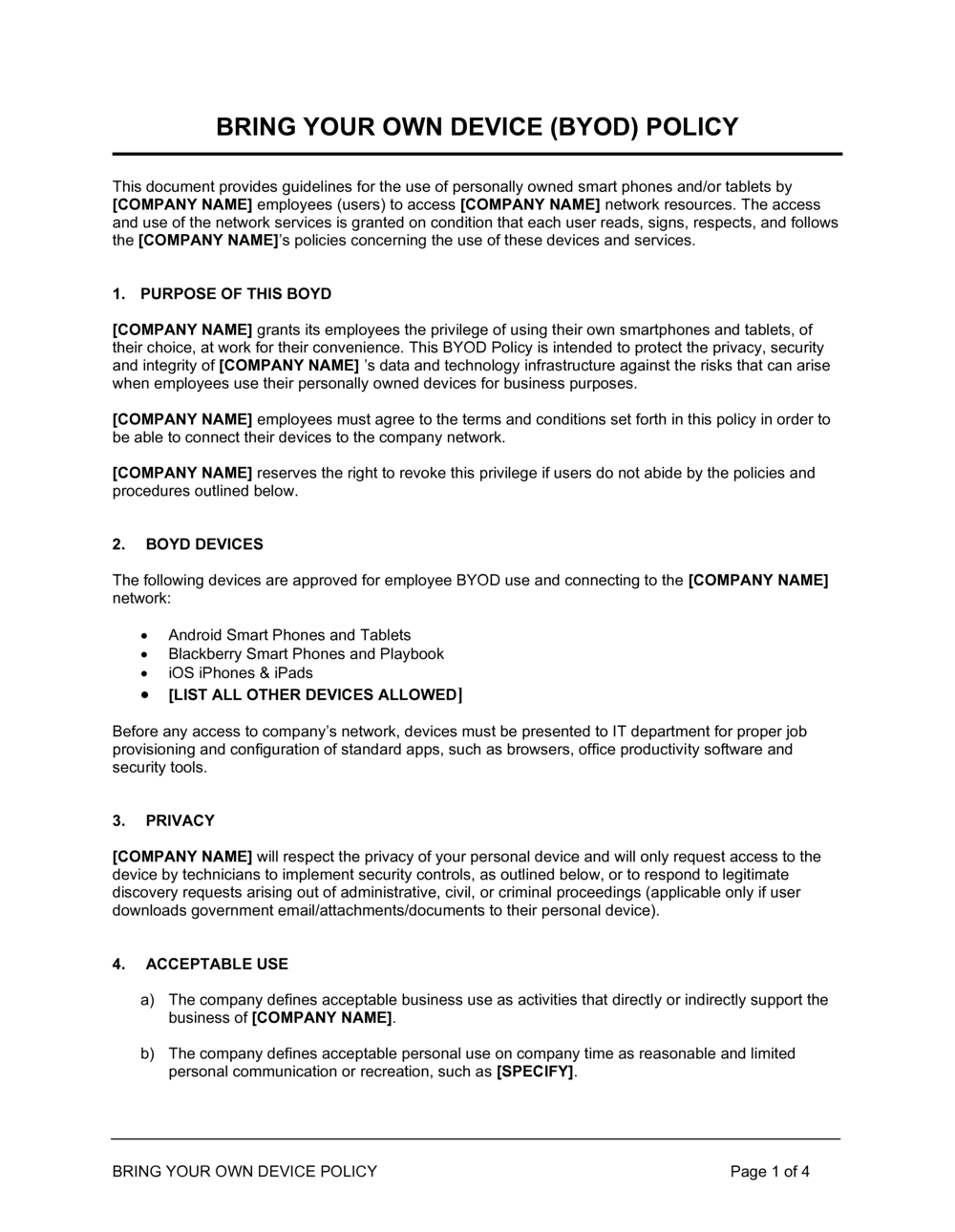
The Ultimate Guide to BYOD Security: Overcoming Challenges, Creating Effective Policies, and Mitigating Risks to Maximize Benefits | Digital Guardian

The Ultimate Guide to BYOD Security: Overcoming Challenges, Creating Effective Policies, and Mitigating Risks to Maximize Benefits - BlazeGuard













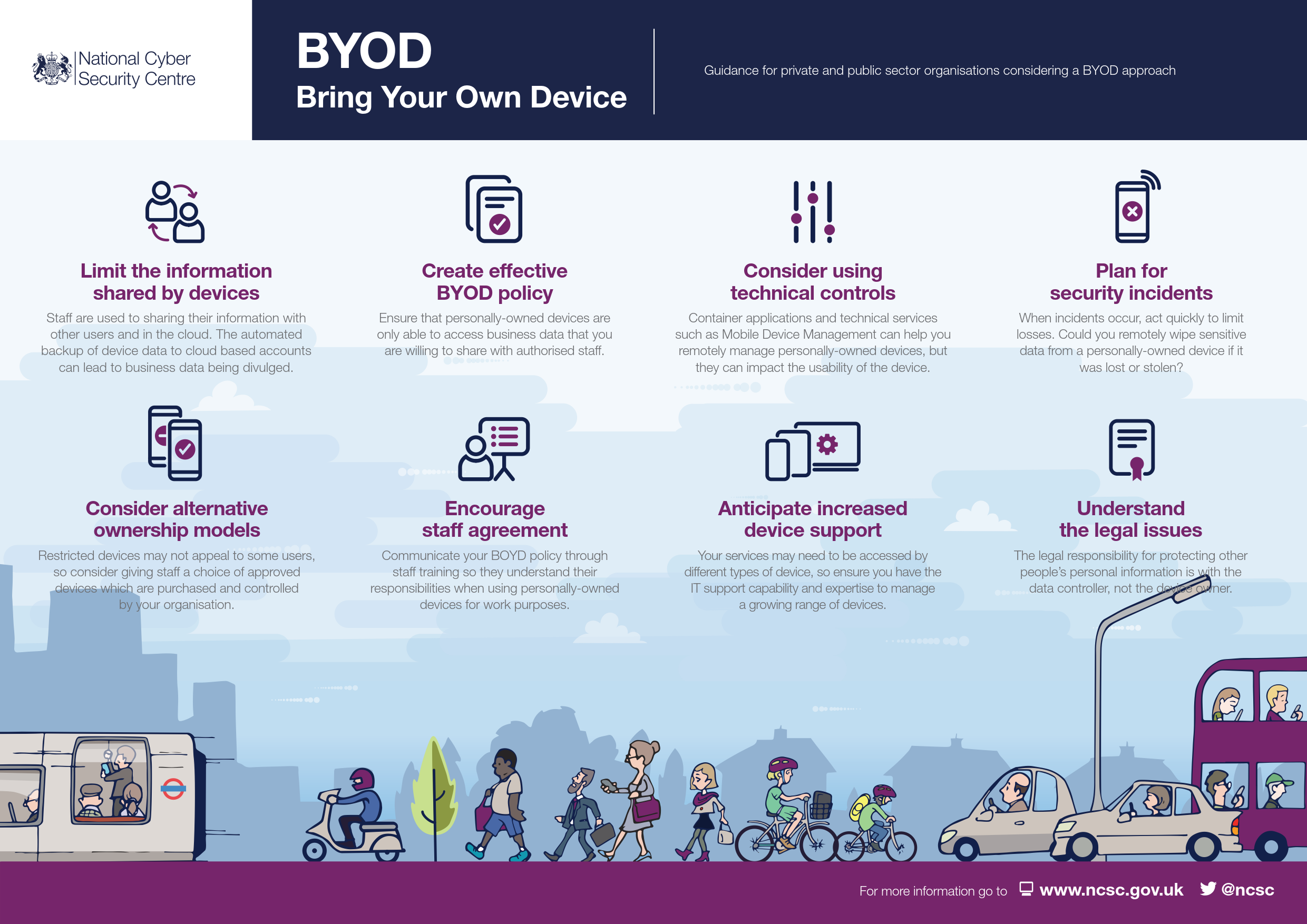







![Withdrawn] BYOD Guidance: Executive Summary - GOV.UK Withdrawn] BYOD Guidance: Executive Summary - GOV.UK](https://assets.publishing.service.gov.uk/government/uploads/system/uploads/image_data/file/31171/byod_infographic_final.png)